OCI bastion allows a restricted and time-limited way to access private endpoints. This could be used for accessing EM database express of DBCS VM DBs. Since most of the cases database would reside in a private subnet, the bastion service provides a convenient way to accessing these services with private endpoints. Only downside is that maximum time to live (TTL) for a bastion session is 3 hours. So this wouldn't be good for 24/7 monitoring (unless creating a new session every 3 hours is not a hazzel). This post shows the steps for creating a bastion session and accessing the EM database express using it.
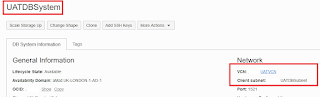
First up some details about the DBCS VM DB setup. The database system resides in a private subnet.
If not already done, enable EM Express for the database. For more info on this refer 2453454.1. In this setup the EM express runs on port 5500.
Access bastion service from the OCI console (found under Identity and security). Give a bastion a name and select the same VCN and private subnet where the databsae resides. These sections shown in red. In addition to above provide a list of IPs or hostname that will access the bastion session. In this case a single IP is given (public IP for the test windows pc shown by whatsmyip). This section is shown in blue.
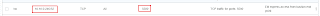
Once the bastion is created make a note of its private endpoint.
Add an ingress rule to the security list associated with the private subnet (where the database resides) using the bastion endpoint as source. This step is not needed if an exiting rule already allows this traffic.
Make a note of the private IP of the database node.
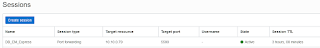
Next create a bastion session by selecting port forwarding as the session type. As the IP address specify the private IP of the database node. Specify the port on which EM express runs, in this case 5500. Finally provide a public key of a ssh key pair. This doesn't have to be the same key used for the database. This key is used only for the bastion session and has no relevence for the database.
Click the menau at the end of the bastion session (three dots at the end) and select copy ssh command. This will copy the ssh command to needed to create the tunnel to the clipboard.
Replace the placeholder values with actual values. Placeholder values include the private key file and the local port. In this case the local port is also set to 5500. If running on windows the power shell could be used to execute the ssh to create the port forwarding ssh tunnel.
Once the ssh tunnel is created access the EM express from the PC browser using localhost as the server.
skip to main |
skip to sidebar















There are two types of researchers. Those who have done something and those who haven't. The latter will say there are 143 ways to do something, and the former will say 142 of them don't work. - Quote from a System V researcher


Labels
- 10.2.0.4 (2)
- 10.2.0.5 (2)
- 10g (37)
- 11.1.0.7 (12)
- 11.2.0.1 (8)
- 11.2.0.2 (22)
- 11.2.0.3 (46)
- 11.2.0.4 (25)
- 11g (48)
- 11gR1 (51)
- 11gR2 (91)
- 12.1.0.1 (16)
- 12.1.0.2 (21)
- 12.2 (5)
- 12.2.0.1 (16)
- 12c (36)
- 18c (11)
- 19c (11)
- 21c (2)
- 23ai (1)
- 3136 (1)
- 4390875 (1)
- 4430244 (1)
- 4483084 (1)
- 4k sector (2)
- 5155885 (1)
- 5447395 (1)
- 6627640 (1)
- 8898852 (1)
- acfs (3)
- acfsload (1)
- acfsroot (1)
- acfsutil (1)
- active database (6)
- active dataguard (10)
- activemq (1)
- add node (5)
- add standby (2)
- adg_account_info_tracking (1)
- admon (1)
- AFD (1)
- afd_dsset (1)
- agent (7)
- alias (1)
- apache http server (1)
- apconsole (1)
- append_values (1)
- aq_tm_processes (1)
- archive gaps (2)
- arcn (2)
- ash (1)
- ASM (53)
- asmcmd (1)
- asmlib (9)
- asmtool (1)
- async (1)
- ATP (6)
- aud (1)
- audit (6)
- auto commit (4)
- auto index (1)
- auto scaling (1)
- auto start (4)
- autoupgrade (4)
- average (1)
- awk (2)
- awr (3)
- AWS (2)
- backup (23)
- basic replication (2)
- bastion (1)
- batch (1)
- bind variables (2)
- bitmap (2)
- blob (5)
- block devices (11)
- blockdev (1)
- blockrecovery (1)
- bonding (2)
- brief (3)
- buffers (1)
- bug (13)
- business intelligence (1)
- cache (2)
- CALIBRATE_IO (2)
- CallableStatement (1)
- cdb (14)
- cfq (1)
- cgroup (1)
- chain (1)
- change port (2)
- check (1)
- checksum (1)
- chkconfig (1)
- chopt (1)
- chunk (1)
- cifs (1)
- client (3)
- clone (8)
- close (1)
- cloud (6)
- Cloud Control (14)
- CLSC_RECEIVE (1)
- CLSRSC-119 (1)
- CLSRSC-180 (1)
- cluster (31)
- clustering factor (1)
- clusterware (29)
- compact (1)
- compatible.asm (1)
- compatible.rdbms (2)
- compress (2)
- compression (4)
- Connect (3)
- connect through (1)
- connection leak (1)
- connection reset (1)
- contention (2)
- controlfile (6)
- convert (5)
- copy (3)
- cost (3)
- cpu (2)
- create_stored_outlines (2)
- cron (1)
- crs (2)
- crs_stat (1)
- CRS-2632 (1)
- CRS-2640 (1)
- CRS-2674 (1)
- crsd.log (1)
- CVE-2012-1675 (2)
- cvu (1)
- database (25)
- datafile (5)
- dataguard (57)
- dataguard broker (16)
- db cpu (1)
- db file sequential read (1)
- db time (1)
- db_domain (1)
- db_securefile (1)
- dbca (3)
- dbcli (4)
- dbcs (5)
- dblinks (1)
- dbms_aw_exp (1)
- dbms_cloud (2)
- DBMS_CSX_INT (1)
- dbms_cube_exp (2)
- dbms_file_transfer (2)
- DBMS_JVM_EXP_PERMS (1)
- dbms_lob (1)
- dbms_outln (2)
- DBMS_REDACT (1)
- dbms_rolling (3)
- dbms_rowid (1)
- dbms_space (2)
- dbms_sqltune (1)
- dbms_stats (1)
- dbshut (1)
- dbstart (1)
- dbua (12)
- dbvisit (1)
- dbw (1)
- dbwn (1)
- ddl (1)
- deadline (1)
- DEFERRED_SEGMENT_CREATION (1)
- definer (1)
- delete node (5)
- deleted (1)
- dependency (1)
- deprecated (1)
- design pattern (1)
- dhcp (1)
- DIA-49802 (1)
- dictionary scripts (1)
- diskmon (1)
- dispatcher (1)
- division (1)
- dmidecode (1)
- dnfs (1)
- DNS (2)
- docker (3)
- downgrade (5)
- DRCP (1)
- DSTv11 (1)
- duplicate (4)
- EBS (1)
- egid (1)
- elevator (1)
- em (15)
- email (1)
- emc (1)
- emctl (2)
- EMD upload error (1)
- encryption (10)
- enq: CF - contention (1)
- enq: HW - contention (1)
- enq: PS - contention (1)
- enq: RC - Result Cache (1)
- enq: TM - contention (3)
- enq: TX row lock contention (1)
- enq: US - contention (1)
- enterprise (3)
- enterprise manager (14)
- error (9)
- exclude (1)
- exp (3)
- expdp (18)
- extended cluster (1)
- extended stats (1)
- external table (1)
- factor (1)
- failover (4)
- fal (1)
- far sync (6)
- FCF (3)
- fdba (2)
- fgac (1)
- filepath (1)
- flashback (4)
- flashback archive (3)
- flashback_time (1)
- flex cluster (3)
- foreign key (6)
- formats (1)
- four digits (1)
- ftp (1)
- gather stats (1)
- gc lost blocks (1)
- gcc (1)
- genoccish (1)
- GIMR (1)
- global database name (1)
- Global Temporary Table (1)
- GNS (1)
- gold image (2)
- GParted (1)
- grid control (7)
- grid infrastructure (67)
- GUID (1)
- haip (1)
- hanganalyze (1)
- hard parse (1)
- hidden parameters (1)
- hostname (2)
- hub node (1)
- IaaS (1)
- IDCS (1)
- identity column (1)
- imp (2)
- impdp (14)
- import_sql_profile (1)
- in-clause (1)
- inbound connection timed out (1)
- incremental (4)
- index (3)
- indexes (2)
- inplace (2)
- input (1)
- ins_emagent.mk (1)
- ins_precomp.mk (1)
- ins_srvm.mk (1)
- INS-30508 (1)
- install (19)
- instance principal (2)
- instance recovery (2)
- interconnect (3)
- internal error (3)
- invisible (1)
- invoker (1)
- iptraf (1)
- iscsi (1)
- iso (1)
- java (17)
- java sinppet (2)
- java7 (1)
- jax-ws (4)
- JDBC (26)
- JDBC Logging (1)
- JI (1)
- jprofiler (1)
- jrockit (2)
- Kcbz_check_objd_typ_3 (1)
- kccsbck_first (1)
- keep (1)
- kernel (2)
- keystore (1)
- kfioTranslateIO03 (1)
- kfod (3)
- kgmgchd1 (1)
- Kkslgbv0 (1)
- kqlindp-bad-user (1)
- ksfd: async disk io (1)
- latch (1)
- latch free (2)
- latch: enqueue hash chains (1)
- Lbrary (1)
- leaf node (1)
- lftp (1)
- lgwr (2)
- LibraryCacheNotEmptyOnClose (1)
- link (1)
- linux (16)
- listener (7)
- lns (1)
- load (1)
- lob (9)
- lobsegment (5)
- local undo (2)
- lock account (1)
- locking (6)
- Log File Parallel Write (1)
- Log File Sync (2)
- log flood (1)
- logical standby (1)
- LT_EXPORT_PKG (1)
- Maemo (2)
- materialized view (2)
- mbean (1)
- memory (7)
- memory_target (2)
- mercury (1)
- metadata (1)
- metalink (1)
- MFA (1)
- MGMT_DB_LL_METRICS (1)
- MGMTDB (1)
- migrate_stored_outline (1)
- Mission Control (1)
- modify (1)
- mongodb (1)
- monitor (2)
- mount (2)
- move (13)
- mtom (1)
- multi-standby (1)
- Multipath (4)
- netca (1)
- netstat (1)
- network (2)
- network_link (1)
- nfs (3)
- nls_date_format (1)
- nls_lang (1)
- node (2)
- Nokia N900 (2)
- nologging (2)
- nomount (1)
- non-asmlib (4)
- non-CDB (9)
- non-default port (1)
- noop (1)
- nosql (1)
- ntp (1)
- null cols (1)
- OALL8 (1)
- OBIEE (1)
- object storage (1)
- occi (1)
- OCI (12)
- ocr (15)
- ocrmirror (1)
- ODCIEXTTABLEFETCH (1)
- ODCIEXTTABLEOPEN (1)
- oel5 (1)
- oel6 (5)
- offline (1)
- OKE (1)
- ol8 (1)
- olap (3)
- OLAPIHISTORYRETENTION (1)
- OMF (1)
- oneway (1)
- ons (4)
- ontology (1)
- oom-killer (1)
- OOP (2)
- opatch (12)
- openfiler (1)
- openvpn (1)
- options (2)
- ora 4031 (1)
- ORA-00349 (1)
- ORA-00933 (1)
- ORA-00942 (1)
- ORA-01031 (1)
- ORA-01078 (1)
- ORA-01460 (1)
- ORA-01652 (1)
- ORA-01858 (1)
- ORA-03137 (1)
- ORA-03186 (1)
- ORA-04063 (1)
- ORA-06512 (1)
- ORA-12504 (1)
- ORA-12696 (1)
- ORA-15061 (1)
- ORA-15081 (1)
- ORA-15477 (1)
- ORA-1555 (1)
- ORA-16713 (1)
- ORA-16816 (1)
- ORA-16856 (1)
- ORA-1691 (2)
- ora-27303 (1)
- ORA-30012 (1)
- ORA-31693 (1)
- ORA-39095 (1)
- ORA-39127 (3)
- ora-600 (3)
- orachk (1)
- oracle (113)
- oracle restart (7)
- ORACLE_OCM (1)
- oracle.plsql (1)
- oracleasm (4)
- OracleConnectionWrapper (1)
- oradebug (1)
- oraInventory (2)
- oralce (1)
- oratop (1)
- os upgrade (4)
- os watcher (1)
- osw (1)
- output (1)
- owl (1)
- PaaS (12)
- parallel DML (1)
- parallel Query (2)
- parse (1)
- partition (1)
- partitioning (1)
- password (3)
- password store (1)
- patch (16)
- Patch 9655006 (1)
- pctfree (1)
- pctversion (1)
- pdb (24)
- performance (11)
- PERFSTAT.STATS$MUTEX_SLEEP_PK (1)
- permissions (2)
- pfile (1)
- php (1)
- php5 (1)
- physical (1)
- physical standby (28)
- PITR (1)
- pl/sql (5)
- policy (3)
- powerpath (1)
- ppk (1)
- PRCR-1079 (1)
- PreparedStatement (3)
- PRIF-31 (1)
- proc (1)
- profiler (1)
- prompt (1)
- protege (1)
- protocol (1)
- PRVF-5150 (1)
- PRVF-5637 (1)
- PSU (7)
- PSU 11.2.0.1.2 (1)
- public (2)
- puschitz (1)
- putty (2)
- qopatch (1)
- query (1)
- rac (92)
- raccheck (2)
- RAID 10 (1)
- RAID 5 (1)
- raw (6)
- rda (1)
- real time sql monitoring (1)
- rebalamce (1)
- recover (5)
- recovery catalog (3)
- redo (2)
- redo block size (2)
- redo sending (2)
- RedoRoutes (1)
- refresh fast (1)
- relational division (1)
- relink (9)
- remap_data (1)
- remote debugging (1)
- remotely (3)
- remove (8)
- rename (4)
- replace (2)
- replication (1)
- resetlogs (2)
- resize (3)
- restore (16)
- restore points (4)
- result cache (5)
- result set (1)
- revoking privileges (1)
- rfs (1)
- rhel4 (2)
- rhel5 (5)
- rhel6 (13)
- rhel7 (10)
- rhel8 (1)
- rman (15)
- RMAN-06025 (1)
- role separation (19)
- roles (1)
- roll forward (3)
- rollback (1)
- rollback_segment_count (1)
- rollover (1)
- row cache lock (1)
- row store (1)
- rpm (5)
- runcluvfy (3)
- sar (1)
- scalar subquery (1)
- scale up (1)
- scan ip (3)
- scan_listener (3)
- SCHEMA_INFO_EXP (1)
- SCN (2)
- script (7)
- search (1)
- sector size (1)
- securefile (3)
- security (8)
- segment size (1)
- sem (1)
- semaphore (1)
- sequence (3)
- services (2)
- session (1)
- session_cached_cursors (2)
- setasmgidwrap (4)
- setuid (2)
- sga (2)
- sgement space reuse (1)
- sh (6)
- shared memory (3)
- shared pool (1)
- shared server (3)
- shm (2)
- shutdown (1)
- silent installation (4)
- single (8)
- skgznpcre3 (1)
- skip (1)
- smbfs (1)
- snapshot standby (1)
- soft parse (1)
- solaris (4)
- spfile (5)
- sql (7)
- sql developer (3)
- sqlldr (1)
- sqlloader (1)
- sqlpatch (1)
- sqlplus (4)
- ssh (5)
- SSL (3)
- standalone (14)
- standard (6)
- standby controlfile (3)
- standby first (1)
- start (1)
- startup (1)
- statm (1)
- stats (3)
- statspack (3)
- status (2)
- stop (1)
- storage (1)
- stored outline (3)
- streams (2)
- support (1)
- swing (1)
- switchover (3)
- swrl (1)
- Sync ASM rebalance (1)
- sysdba (2)
- systemstate (1)
- tablespace block size (1)
- tablespaces (7)
- tail (1)
- tcps (3)
- TDE (3)
- template (1)
- temporary tablespace (2)
- Text (1)
- tfactl (1)
- time synchronization (1)
- time zone (2)
- timesten (1)
- tns (4)
- tomcat (2)
- trace (1)
- transient (1)
- transport (2)
- transportable tablespaces (2)
- truststore (1)
- ubunut (1)
- UCP (8)
- udev (4)
- undo (4)
- up2date (1)
- update (2)
- upgrade (58)
- uploadXMLFiles (1)
- urandom (1)
- use_stored_outlines (2)
- useful (1)
- utl_mail (1)
- validate (1)
- vault (1)
- verifier (1)
- vi (1)
- VIP (2)
- virtual (1)
- virtualbox (3)
- visible (1)
- vktm (1)
- vnc (3)
- vncr (1)
- vote (14)
- wait (3)
- Wait Events (7)
- wallet (1)
- web service (1)
- web site (1)
- weblogic (1)
- wget (1)
- windows (1)
- wm_concat (2)
- work around (1)
- writes (1)
- xdb (1)
- xml (1)
- XML-20108 (1)
- yum (3)
About Me
Downloads












Quick Response

Popular
- ORA-00800: soft external error, arguments: [Set Priority Failed], [VKTM], [Check traces and OS configuration]
- Adding a New Physical Standby to Existing Data Guard Setup
- Using UR=A to Connect to Databases in Nomount Mode
- Enabling Automatic AWR Snapshots on PDB
- Upgrading Enterprise Manager Cloud Control from 13.5 to 24.1 - 2
- Encrypting / Decrypting Tablespaces Online / Offline
- ORA-16713: The Oracle Data Guard broker command timed out When Changing LogXptMode
- DIA-49802: missing read, write, or execute permission on specified ADR home directory
- Upgrading Enterprise Manager Cloud Control from 13.5 to 24.1 - 1
- GUID Directory Not Created for PDBs During Full Restore in 12.1.0.2